Utilities Module
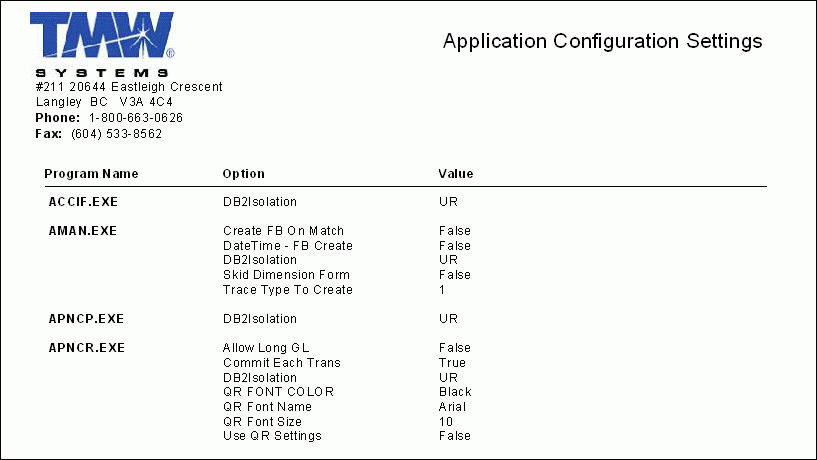
CONFIG.RPT
This report is used in conjunction with the Application Configurator program (CONFIGEXPLORER.EXE), and will produce a list of all the Application Configuraiton options and their current setting, broken down by TruckMate program. This report is about 20 pages long.
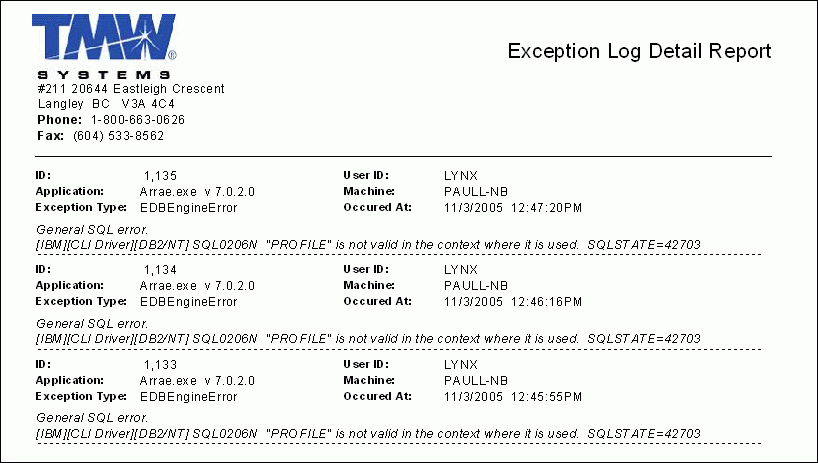
EXCEPTDTL.RPT
The Exception Log Detail report is run from the Exception Viewer program (EXCEPTVIEWER.EXE), and will produce a list of all the exceptions (errors) currently logged by that program in a Detailed format. This report can be quite long if the Exception Viewer application’s records have not been cleared for some time.
EXCEPTSUM.RPT
The Exception Log Summary report is run from the Exception Viewer program (EXCEPTVIEWER.EXE), and will produce a list of all the exceptions (errors) currently logged by that program, broken down by 'Date of Occurrence'.

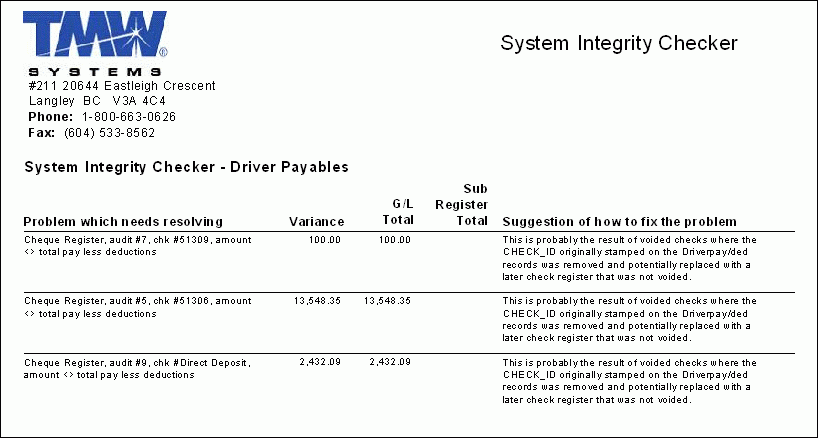
SYSCHECKER.RPT
This report is used in conjunction with the System Integrity Checker program (SYSCHECKER.EXE), and will produce a text-based listing of all the errors/exceptions that have been logged for your system.
| Depending on how frequently the records are viewed and deleted from within the SYSCHECKER.EXE application, this report can become very lengthy. |
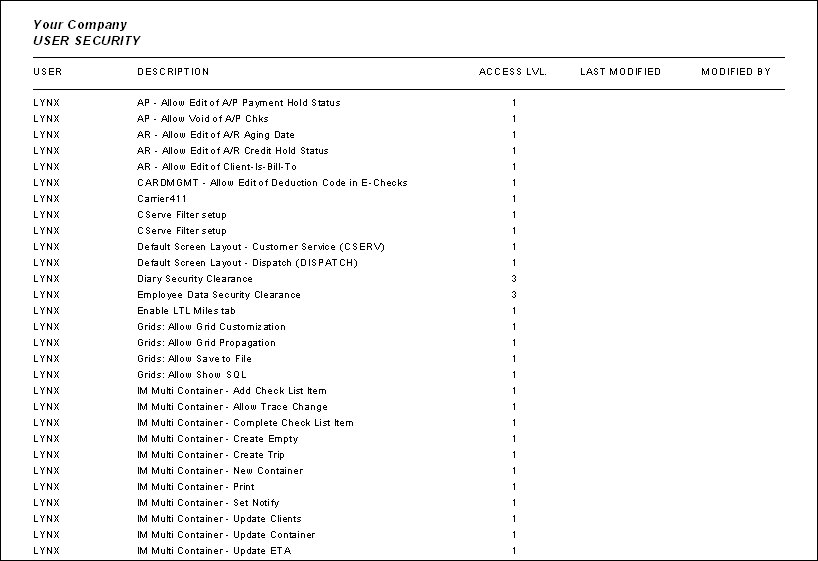
USER_SECURITY.RPT (251)
The User Security report is run from the Crystal Report Launcher program (CRRUN.EXE), and will list all of the currently configured security settings on a per-user basis. When the report is loaded, you will be asked to provide a unique 'User ID', or to gather the security information for all users. The report displays nearly all options available in the Security Setup program, and displays an 'ACCESS LVL' for each option, with the following general values:
-
1* (Enabled): User has access to the security option.
-
0* (Disabled): User does not have access to the security option.
You may see other values, such as '3' and a 'Security Clearance' description, but these refer to specific settings on the Security Setup program > Security > Clearance Tab. For the most part, '1' (Enabled) and '0' (Disabled) are the options that are most useful in getting a general idea of a users' access level.